7 Mobile App Security Tips To Keep Your Users & Platform Safe
Mobile app security needs to be a front-and-center concern for everyone who has a hand in developing or supporting applications, platforms, and infrastructure as failure to make a safe product opens doors for all hell to break loose for the users, businesses, or both. In light of the recent breach by supposed Russian hackers into US government systems, it seems like a great time to discuss digital safety. So, in the following, we’re going to revisit some of the most important security measures that need to be in play as we move through this new decade.
The anatomy of an attack and why authentication is key for mobile app security
The preliminary goal of most attacks is to get a hold of user credentials as this gives an attacker the power to abuse the privileges of the account they exploit. For example, one thing we’ve seen surface in recent times is the fraudulent use of Facebook accounts for payment app scams after they’ve been compromised – once the account is taken over, the person on the other end posts something to the effect of “Drop your Cash App name to get paid” which will initiate a chain reaction when a view takes the bait. What typically follows is a message exchange where the user is: fooled into sending money to the fraudster (e.g. “if you send me $5 now, I’ll send you $500 in 20 minutes”), convinced to reveal some other crucial piece of data, or provided with a link to an official-looking site that’s actually a phishing attack.
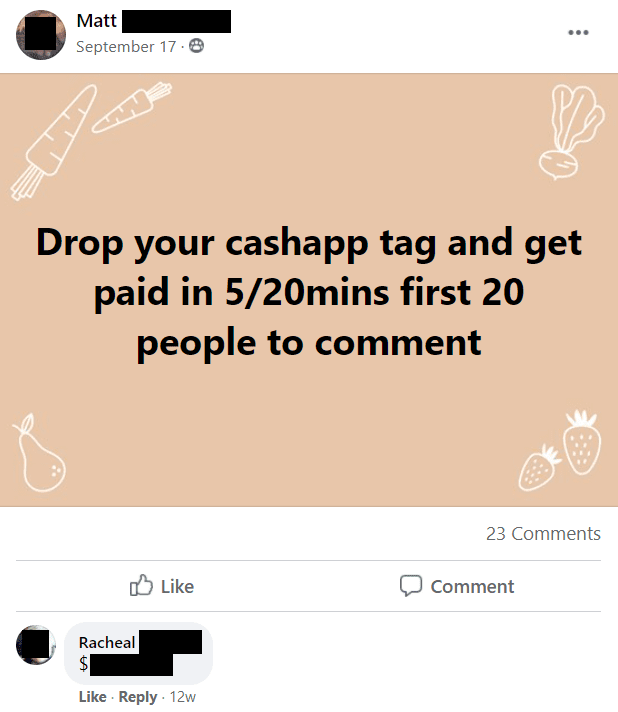
These kinds of scams aren’t pursued by authorities for a couple of reasons, namely because they’re just hard enough to trace and don’t steal enough money in the grand scheme of things to warrant any kind of legal action. Too, when a Facebook account is breached, as sad as this is to say, the outcome is mostly a breach of privacy on the user’s end. Further, most users aren’t compromised through sophisticated “trickery” like when a hacker cleverly captures then remotely emulates a session – because a significant portion of users don’t take advantage of Facebook’s built-in 2FA (or third-party tools, for that matter) an attacker simply needs a user name and password combo to access an account.
Anymore, on the user end, not taking advantage of such authentication mechanisms is the digital equivalent of living in a high-crime neighborhood and leaving your home completely open.
Taking over a regular user account on social media might be awful for the affected person but it’s not a big threat to the platform itself. It’s a whole other story when someone with a more privileged account is compromised. When higher-level accounts are breached, the potential for harm is far greater.
Interestingly, the solution to this mobile app security problem for both the run-of-the-mill user and the system admin is the same. By applying mechanisms that provide a second layer of authentication, whether an app like Authy or a unique code sent to a verified email or mobile number, this greatly reduces the likelihood an attack will succeed as this requires the attacker to have control of another account or physical access to a specific device.
Beyond account level security, tech on the backend like the APIs used to push and pull data between systems need to be locked down to prevent the possibility of exposing sensitive data. Depending on your software architecture and the function of the APIs you use, security certificates should be used when transmitting most user information between systems. For example, when user credentials are called on by an API to send or retrieve information, this and any personally identifiable information should be encrypted to prevent exposure of sensitive data.
7 tips for mobile app security to keep in mind
By keeping the following best practices in mind, your app will be in better shape to ward off attacks that could seriously affect your users or platform.
1. Use third-party login tools to authenticate users
We currently recommend using products like Sign in with Apple for a couple of reasons which you can learn more about by reading the blog in the link. Here, the iCloud Keychain is used to store the user’s session token removing any possibility that the user’s credentials can be compromised should an attacker gain access to either the user’s device or the platform. Too, Apple passes off a randomly generated email to platforms when users sign up which virtually eliminates the possibility that this information would be exposed in the event of an attack.
2. Limit access to your infrastructure
It’s a given that you don’t want your users to be able to perform administrative tasks or access anyone else’s private information, such as personal information other users provide for their account. It’s also important to limit who can access your backend systems. As such, limit backend access to resources by tailoring user privileges specific to the role they perform – in the event a dev account is compromised, this provides some level of damage control by limiting what an attacker can functionally access. Make sure to employ 2FA wherever possible and also make sure that your Git repositories are private.
3. Use end-to-end encryption throughout your app
Before a user even logs into an app, they should be protected by some form of encryption as they log in – if you’re not using Sign in with Apple or another good third-party product, at least make sure that you’re encrypting your login page. From there, everything the user does should be wrapped in encryption, from in-app messaging to interacting with other elements where they may be sharing personal information. Make sure that your encryption keys aren’t being stored locally on the user device or your servers for optimal mobile app security.
4. Offer a simple UI
Create trust with your users by developing a UI that’s consistent throughout and well labeled. This prevents scenarios where a user might unwittingly share private information to a public field. For example, your users should feel confident that the information they are required to share to complete registration won’t be publicly visible.
5. Lockdown user sessions
Today, the most secure way to ensure that a user’s session isn’t compromised is through the use of tokens. App tokens and passwords should never be stored in the code itself, the user device, or the server. Instead, unique tokens should be generated after a successful login using MFA then stored using a service like iCloud Keychain or Google’s KeyChain.
6. Enforce API authentication
Your APIs handle a lot of the heavy in transmitting data between systems. For systems subject to data compliance regulations like HIPAA, it’s especially critical that APIs are privatized and mandate authentication in every exchange for ideal mobile app security. This prevents situations where an attacker gains access to an API as this will essentially prevent them from being able to do anything meaningful, such as pulling data from a patient file.
7. Audit and test your code
You need to regularly audit your code for security vulnerabilities – over time, certain methods become outdated, leaving apps prone to several different kinds of attacks including injection, cross-site scripting (XSS), man-in-the-middle (MitM), or credential stuffing, to name a few. Even if your code “looks right” devs should take some time to try and breach their product using these techniques. Sometimes, little nuances in code prove to be less secure than first though, thus opening the door for successful outside attacks.
Building secure products is our number one priority
We are a forward-thinking group of technology experts who build solutions for not just the modern era, but with the future in mind. While building a functional product is the goal, lacking security will eventually lead to a lack of user trust and ultimately, the demise of your reputation. Feel free to reach out to us to learn how we can build a digital product that’s both valuable to your users and secure.









